Since 2013, Krescendo has achieved the ISO27001:2013 certification for its information security management systems and risk management processes.
As one would expect, the ISO standard requires us to have well-managed controls in place for physical security, access controls, and underlying communication protocols.
However, ISO27001 is designed to cover much more than just IT, including
- Policies
- Asset management
- Supplier relationships
- Human resources
- … and many more areas.
As CTO, I am responsible for how we embrace a security development lifecycle to support the construction of our software and web apps. At Krescendo, security takes a central role. As a software company we see security as being our top priority.
Security industry analysts estimate that 70% of attacks are aimed at applications, while only 30% target the underlying infrastructure (network and host).
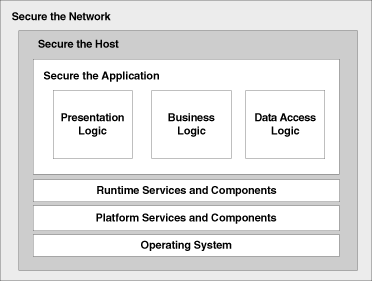
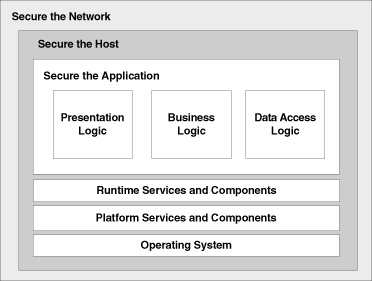
To secure the network and host layers, we rely on third-party vendors, e.g.
- Router
- Firewall
- Operating system
- Web server
- Database
Here our main responsibility is to ensure we have the correct configurations in place and apply all the latest security patches.
For the web applications, it’s critical we have established security requirements in each phase of software development and assigned activities for each role, including our management team.
What is the Security Development Lifecycle?
Over the years, software firms have initiated and enhanced several different approaches to software development (Waterfall, Agile, etc…), unfortunately these offer little support for security requirements.
A security development lifecycle helps developers build more secure software and address security compliance requirements while reducing development costs.
The leading security development lifecycles are Microsoft’s SDL and OWASP’s CLASP. Both approaches acknowledge that training is very important. Everyone in the team (and I would add the whole organization) should receive education on security awareness and possible vulnerabilities.
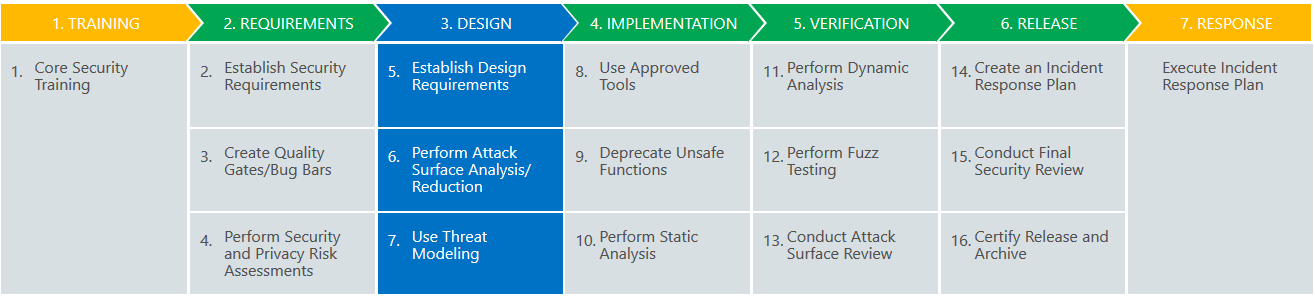
In general, SDL (shown above) offers a well-guided process that focuses on security as a part of software quality.
CLASP addresses security from a broader perspective and can be flexibly tailored to the specific software development methodology. Krescendo chose CLASP as a better fit to the Agile project management methodology we use.
In CLASP, each role has a specific set of activities and tools. For brevity the more relevant roles and activities are:
| Project Manger | Promotes awareness and monitor metrics. |
|---|---|
| Developer | Understands OWASP Top 10 and ensures code is secure. |
| Security Auditor | Performs periodic web app scans and static code analysis. |
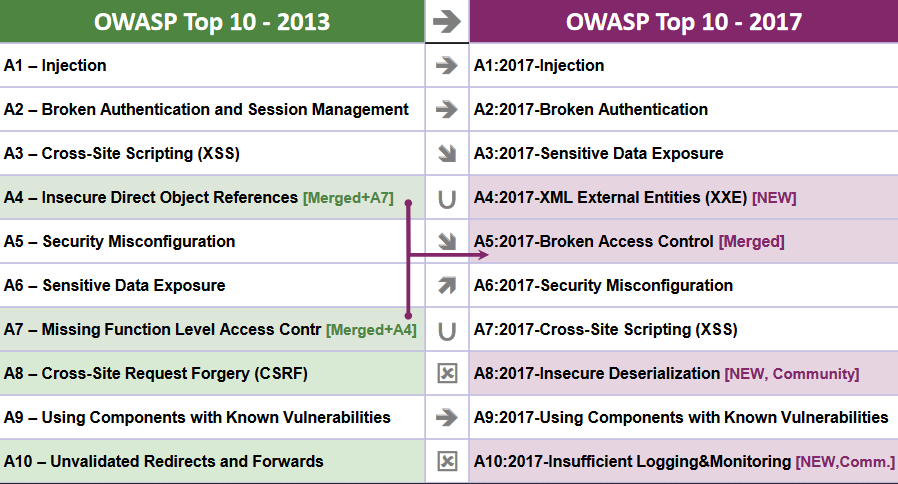
OWASP Top 10
What really counts is training and awareness. Open Web Application Security Project (OWASP) is one of the most respected authorities in the field of web application security and provides an up-to-date list of the most critical vulnerabilities that all roles should be aware of and developer should prevent them.
The latest version is 2017:
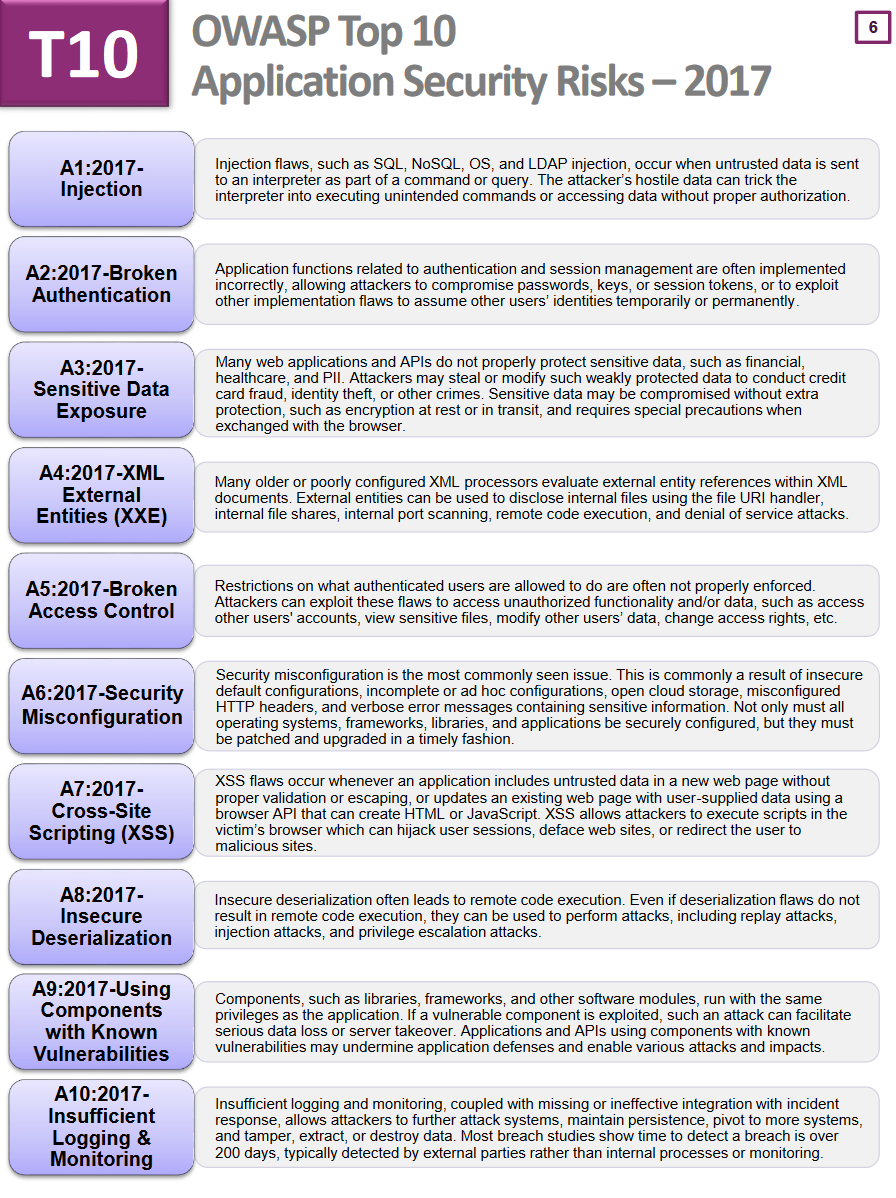
The 2017 version had several changes compared to the previous version (2013) due to fundamental changes in technology and architecture in the last few years (microservices, single page applications…).
External Audit
Krescendo performs internal scans before code is released to test and production. Periodically the applications are also externally audited by clients and third-party companies to
- Confirm that our adopted process are working well.
- Confirm no medium/high vulnerabilities are exposed to end users.
LiveDataset has been externally scanned by two well-known accredited security firms in the last 2 years.
Both reported zero medium/high vulnerabilities.
We encourage clients to involve their IT security and risk management teams at an early stage of every project. If IT security is treated as just a hurdle to signed off at the last moment it can delay a project.
We recommend approaching the IT security early, so they have time to understand the business context, they can make recommendations, and they have time to schedule the necessary checks.
References
In part 2, I will go into more details on how the CLASP methodology impacts our everyday work and how we do web app scanning and static code analysis.